Disable Viral and internal plans
This is the next part of our mini series called “Admins Essentials” covering all the activities that an Admin should have done at least once or needs to do re-occuring. This time we check out what viral and internal licensing plans are, and why we should disable them 🙂
The Catchy Introduction: The Danger of the Invisible Licenses
Imagine discovering that half your organization has unknowingly signed up for a free trial of a tool you’re supposed to govern. Sounds like a sci-fi dystopia, right?
In the world of Power Platform, this dystopia has a name: Viral and Internal Plans. They’re trial licenses designed to empower users but can easily spiral out of control, creating headaches for administrators. Let’s unravel what these plans are, why they’re risky, and—most importantly—how to regain control.
What are viral and internal plans?
Both viral and internal plans share a noble goal: enabling users to explore Power Platform without friction. But in practice, they can wreak havoc on governance. These trial licenses often bypass traditional oversight mechanisms, leaving administrators in the dark about who’s accessing what—and for how long.
-
Viral Plans: These are trial licenses granted automatically when a user accesses a Power Platform resource (like a shared app or flow) without having the required license. This “viral” nature comes from its ability to spread within the organization as more users interact with shared resources.
-
Internal Plans: These are also trial licenses, but they are explicitly initiated by a user, such as when someone signs up for a Power Platform trial through the Microsoft website or admin portal.
Once again we have a classic Shadow IT mechanism with users getting licenses without the admin knowing about this. Once again, I want to give users the opportunity to work with Power Platform, but when I’m responsible for security, I need to know what’s going on. And that leads us to the question…
Why Are They Dangerous?
When licenses are handed out like free candy, it’s easy to lose track of who has what. This can lead to apps and flows relying on trial licenses that suddenly expire—causing disruptions for end-users and leaving admins scrambling for solutions:
- Lack of Visibility: Licenses are granted without prior admin approval.
- Shadow IT: Users can build critical apps or flows with trial licenses, creating unsupported dependencies.
- License Sprawl: These plans muddy the waters when analyzing actual license usage, making budgeting and compliance harder.
- Security Gaps: Viral plans might inadvertently grant access to sensitive data or environments.
when I’m responsible for security, I need to know what’s going on
PowerShell to the rescue
Fortunately, taming this licensing chaos is simpler than you might think. With a few PowerShell commands, you can disable the auto-issuance of these plans and bring licensing back under control. It’s, as usual, not the amount of effort you need to put it, but you have to be aware that this is even a thing!
For this we will need the Microsoft.PowerApps.Administration.PowerShell module, which means, we will need at least the Power Platform Administrator admin role for this. If you are new to PowerShell, check out this Beginner’s Guide, or if you need help with modules, click on this blog.
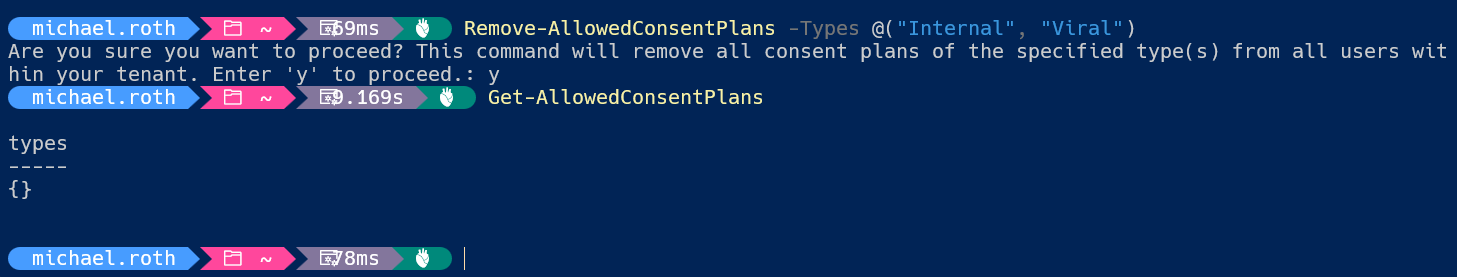
You can disable them separately if you want to, yet I recommend to deactivate both. As an Administrator you are still able to grant trial licenses afterwards and you can even switch these plans back on, if you need to. So you don’t have to worry that your actions might not be reverseable. They are.
##Sign in to the PowerShell module
Add-PowerAppsAccount
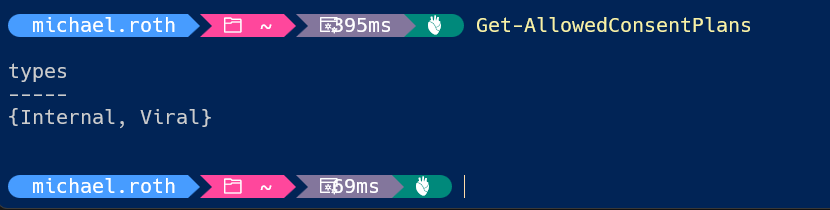
##Check the current allowed plans
Get-AllowedConsentPlans
##Remove the Internal and Viral plans
Remove-AllowedConsentPlans -Types @("Internal", "Viral")
This is a quick and easy fix for this problem. If you need to enable then again, then your code looks pretty similar:
Add-AllowedConsentPlans -Types @("Internal", "Viral")
The extra chapter
But wait, there’s more ☝️
Now that you’ve turned them off, how do you make sure you don’t have any of these plans on the tenant yet?
Fear not, I got you covered.
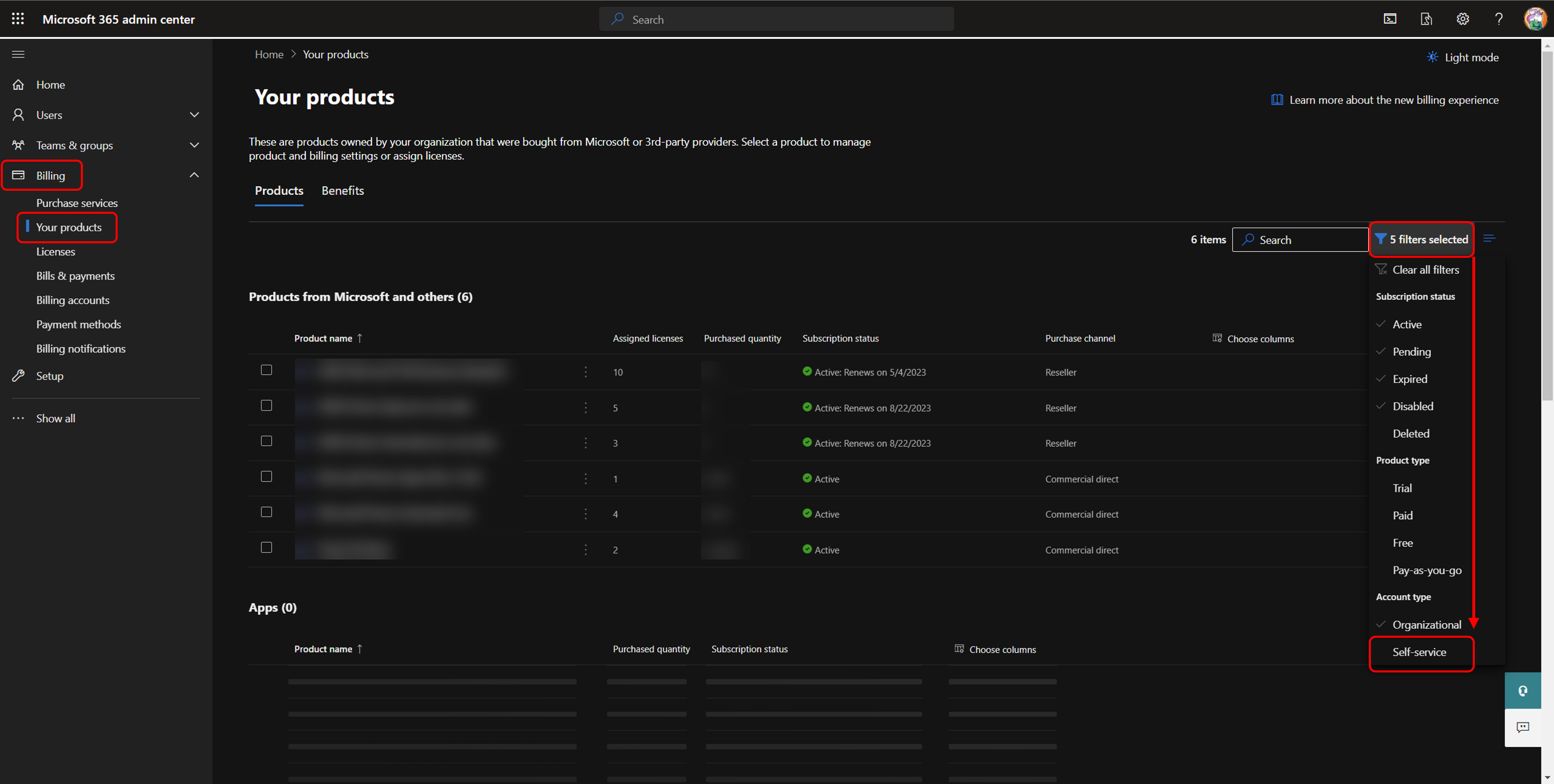
Hop over to the (M365 admin center)[https://admin.microsoft.com/] and select Billing –> Your Products. Did you ever notice that on the very right hand side of the screen a filter is pre-selected? No? Well, now you know. Click on that filter and down at the bottom you can include “Self-service” licenses. When you check this, you can see if you have any on the tenant, and whom they are assigned to.
Hint: You have to be Global Admin, Global Reader or Billing Admin. If you are not, you should be good friends with at least one of them
Conclusion
Once again, a super short blog. It’s not about the amount of effort, but that you are aware of this. Power Platform is all about empowerment—but as administrators, it’s our job to balance freedom with responsibility. By understanding the risks of viral and internal plans and taking proactive steps, you can ensure your organization’s Power Platform journey is smooth, secure, and stress-free.
If you want to learn more about plans and how they work, check Thibualt Joubert’s blog about this.
If you’ve heard me talking about Power Platform Governance 101 on an event, watch out for more posts tagged with “Admin’s Essentials”, that’s where I explain all the important things that you need to be aware of ⚠️
Thanks a lot for reading, and if you have comments, questions, or remarks, feel free to contact me on social media. I’m happy to chat and help and learn 😉
Michael on Bluesky and LinkedIn
Thank you for reading!